通过Wireshark抓包软件来分析计算机网络中的HTTP、TCP、ICMP和ARP相关内容,来进一步加深理解相关知识
HTTP
HTTP超文本传输协议 (hypertext transport protocol),它允许将超文本标记语言(HTML)文档从web服务器传送到客户端的浏览器上。
研究HTTP协议的几个方面:
- 基本的GET/response交互
- HTTP消息格式
- 检索大型HTML文件
- 检索带有嵌入式对象的HTML文件
- HTTP身份验证和安全性。
实验操作步骤及结果
1.The Basic HTTP GET/response interaction
步骤
- Start up your web browser.
- Start up the Wireshark packet sniffer, as described in the Introductory lab (but don’t yet begin packet capture). Enter “http” (just the letters, not the quotation marks) in the display-filter-specification window, so that only captured HTTP messages will be displayed later in the packet-listing window. (We’re only interested in the HTTP protocol here, and don’t want to see the clutter of all captured packets).
- Wait a bit more than one minute (we’ll see why shortly), and then begin Wireshark packet capture.
- Enter the following to your browser http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file1.html Your browser should display the very simple, one-line HTML file.
- Stop Wireshark packet capture.
实验结果
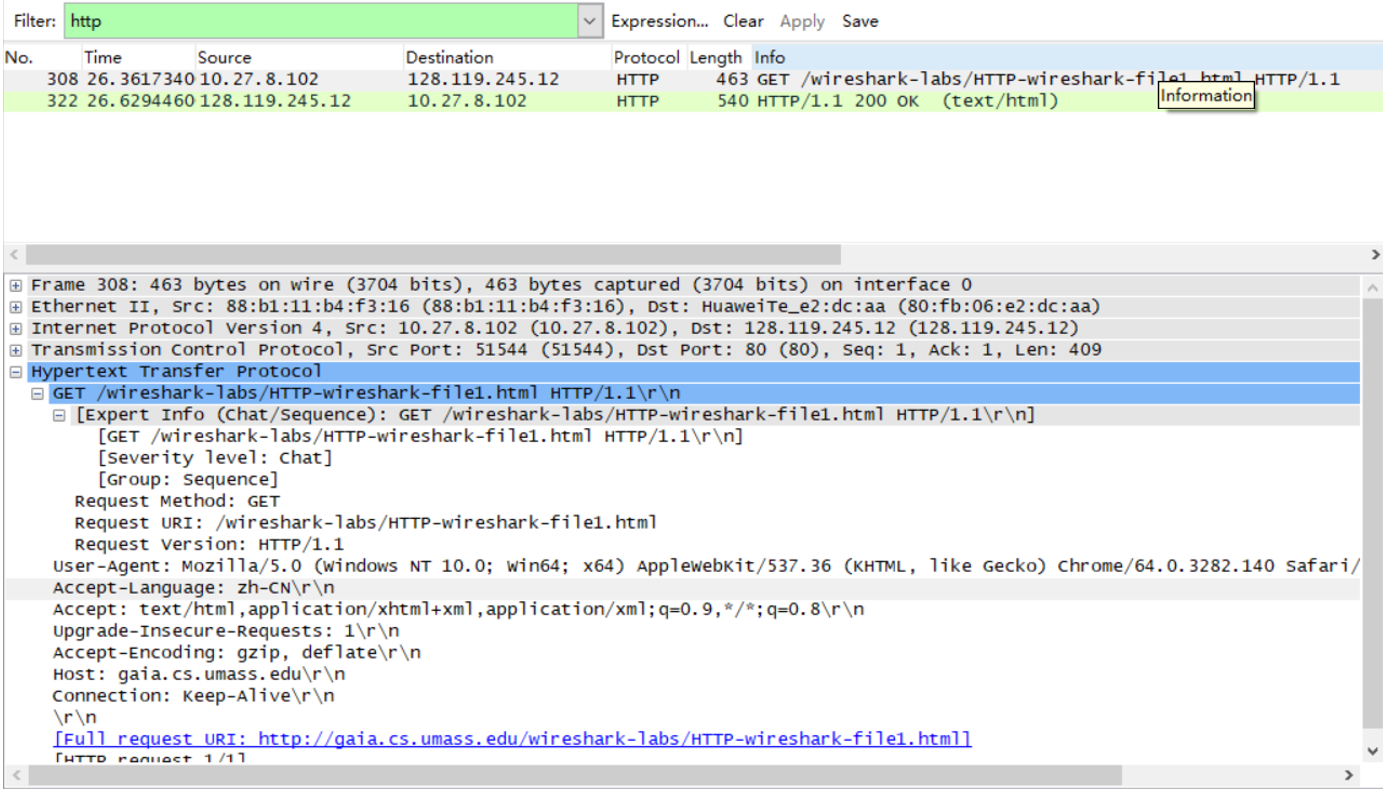
问题回答
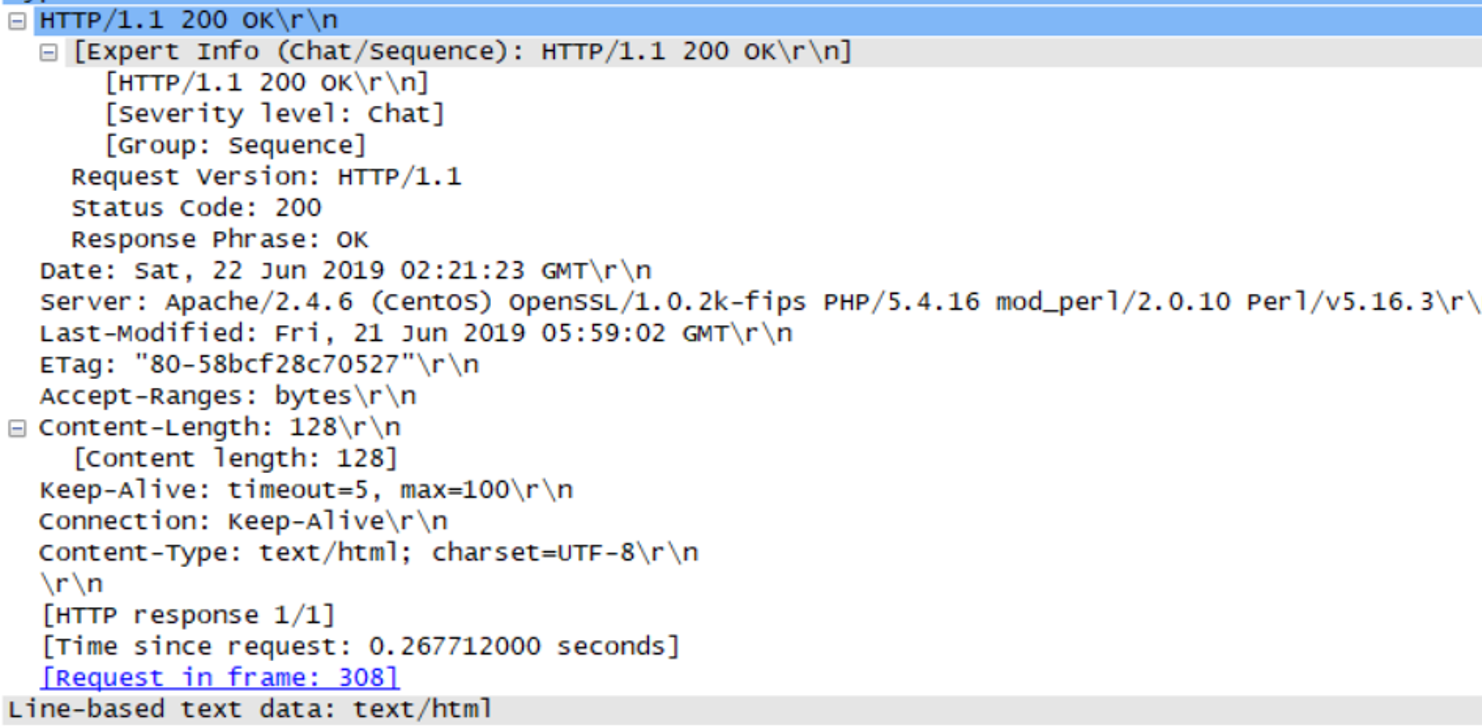
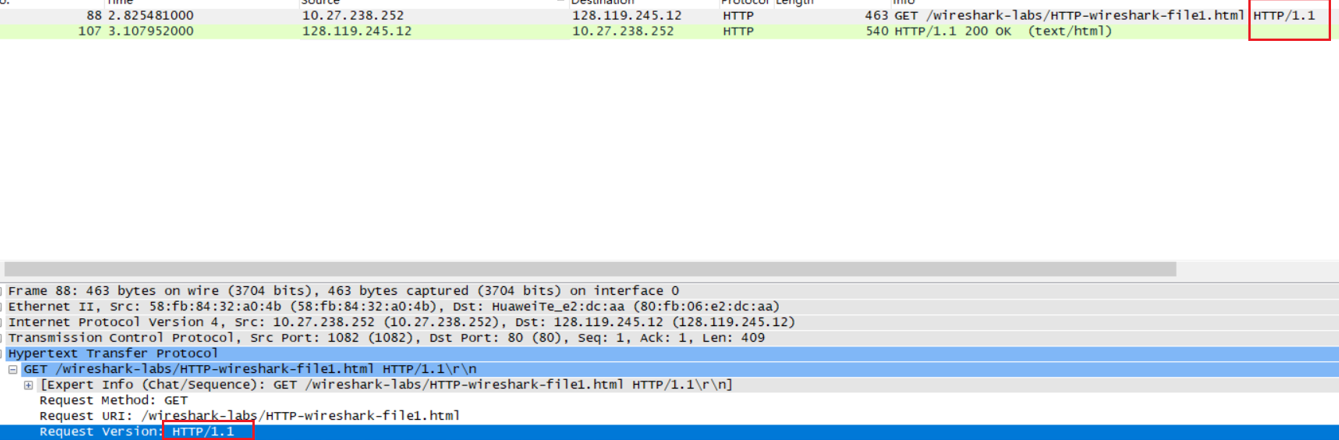
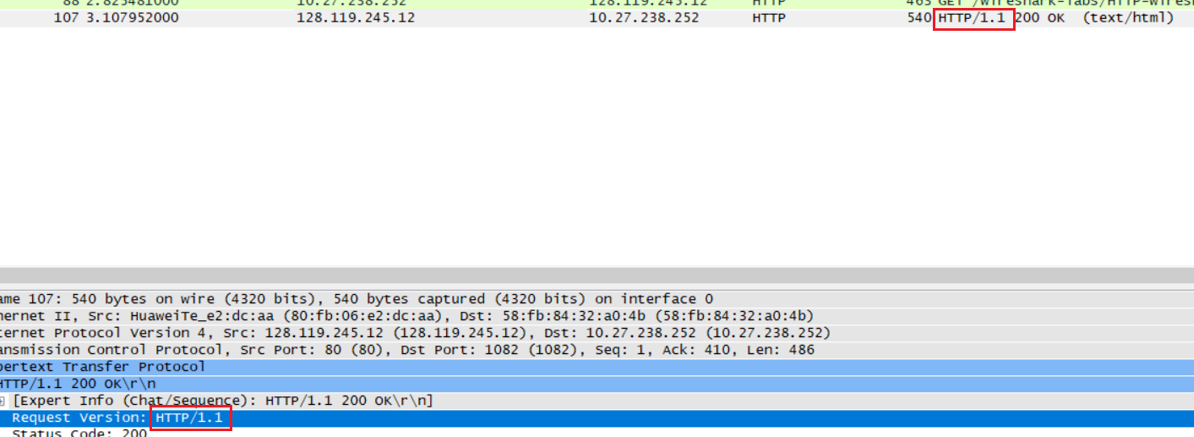
Is your browser running HTTP version 1.0 or 1.1? What version of HTTP is the server running?
我的浏览器运行HTTP1.1
服务器运行HTTP1.1
What languages (if any) does your browser indicate that it can accept to the server?
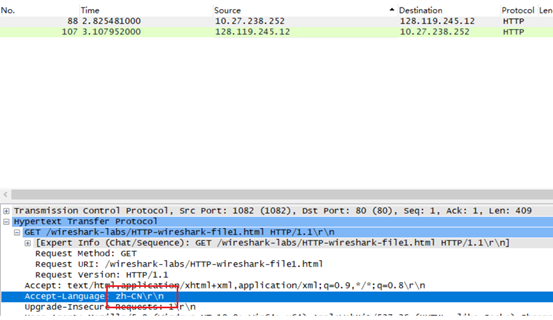
支持的语言有zh-CN(简体中文)
可能产生的情况有Accept-Language: fr-CH, fr;q=0.9, en;q=0.8, de;需要注意的是q的值代表优先顺序,用相对质量价值表示,又称为权重。
What is the IP address of your computer? Of the gaia.cs.umass.edu server?
我的IP地址为10.27.238.252
服务器的IP地址为128.119.245.12

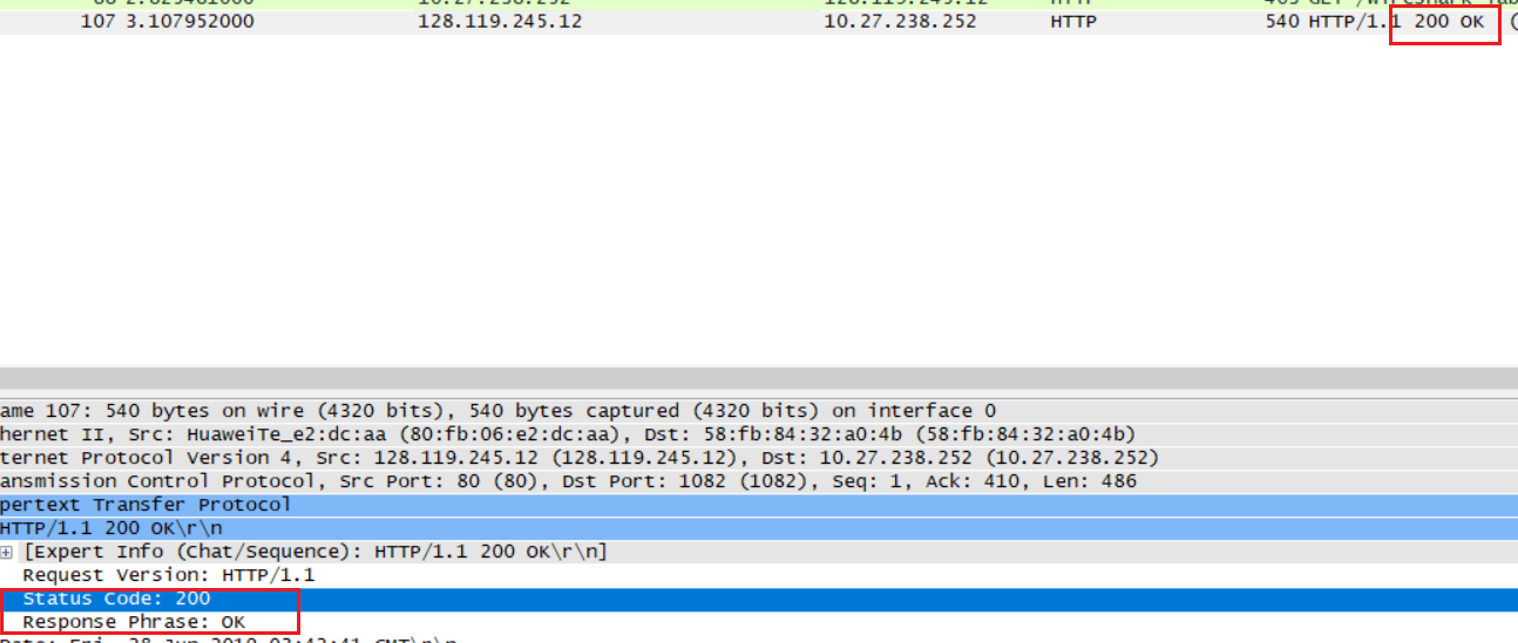
What is the status code returned from the server to your browser?
服务器返回的是200 OK
When was the HTML file that you are retrieving last modified at the server?
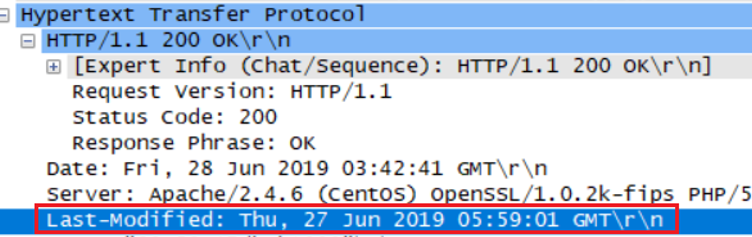
最后修改时间是2019年6月27日 星期四 05:59:01
经过查阅相关资料进一步了解得浏览器第一次请求一个URL时,服务器端返回状态是200,同时last-modified属性标记此文件在服务器端最后被修改的时间。客户端第二次请求此URL时,根据HTTP协议的规定,浏览器向服务器请求if-modified-since报头,询问该时间之后是否有被修改过,若没被修改过的话,返回HTTP 304(NOT Changed)状态码,从而达到节省资源的作用。
How many bytes of content are being returned to your browser?
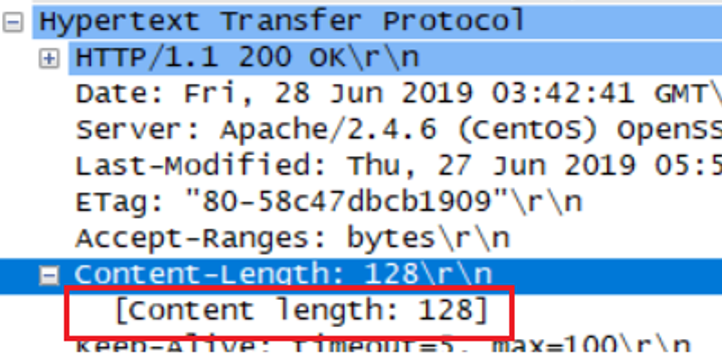
content length:128
By inspecting the raw data in the packet content window, do you see any headers within the data that are not
displayed in the packet-listing window? If so, name one.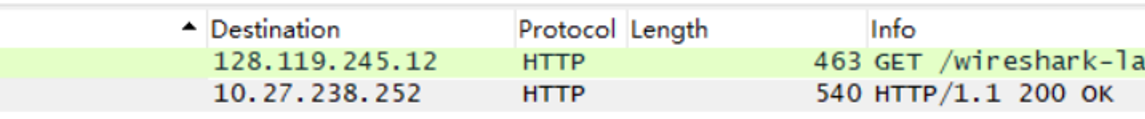
没有,仅有以上的两个http。
2.The HTTP CONDITIONAL GET/response interaction
步骤
- Start up your web browser, and make sure your browser’s cache is cleared, as discussed above.
- Start up the Wireshark packet sniffer
- Enter the following URL into your browser http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file2.html Your browser should display a very simple five-line HTML file.
- Quickly enter the same URL into your browser again (or simply select the refresh button on your browser)
- Stop Wireshark packet capture, and enter “http” in the display-filter-specification window, so that only captured HTTP messages will be displayed later in the packet-listing window.
- (Note: If you are unable to run Wireshark on a live network connection, you can use the http-ethereal-trace-2 packet trace to answer the questions below; see footnote 1. This trace file was gathered while performing the steps above on one of the author’s computers.)
实验结果
问题回答
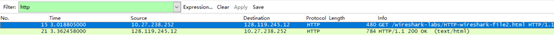
Inspect the contents of the first HTTP GET request from your browser to the server. Do you see an “IF-MODIFIED-SINCE” line in the HTTP GET?
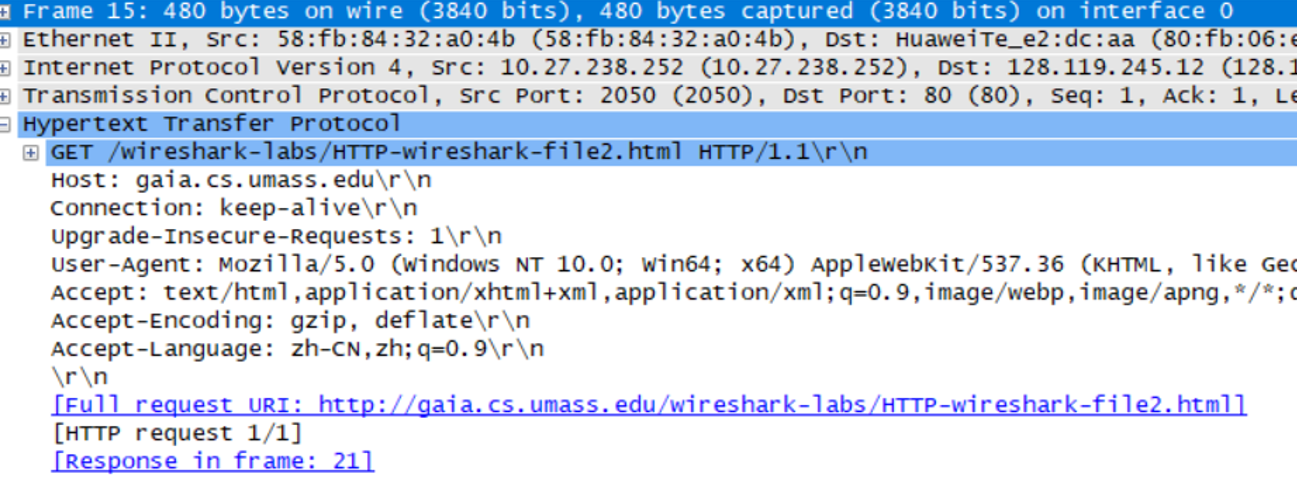
未找到,如第5点中所说的,IF-MODIFIED-SINCE是用于第一次之后再返回时来检查是否有新的更新的。
Inspect the contents of the server response. Did the server explicitly return the contents of the file? How can you tell?
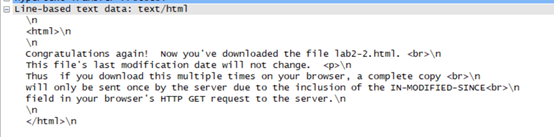
在Line-based中以html格式返回网页中内容
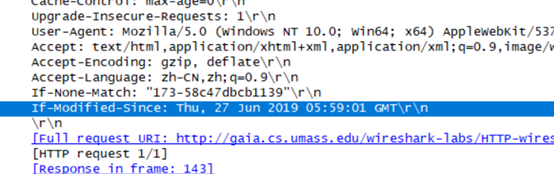
Now inspect the contents of the second HTTP GET request from your browser to the server. Do you see an “IF-MODIFIED-SINCE:” line in the HTTP GET? If so, what information follows the “IF-MODIFIED-SINCE:” header?
当第二次打开网页时,浏览器会根据上次打开这个网页中的last-modified以if-modified-since的内容发送,来检查是否在这个时间之后有没有更新,如果没有更新的话,则调用本地cache缓存。
What is the HTTP status code and phrase returned from the server in response to this second HTTP GET? Did the server explicitly return the contents of the file? Explain.
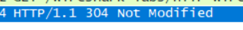
返回304,not modified,表示在last-modified-since服务器没有修改内容,即调用本地缓存即可,当然服务器也不再显式返回文件中的内容(server don’t explicitly return the contents of the file)
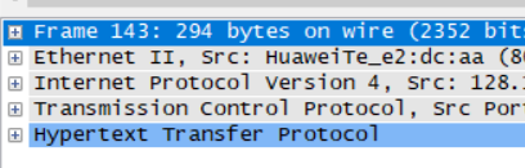
没有Line-based text/html这一项了
3.Retrieving Long Documents
步骤
- Start up your web browser, and make sure your browser’s cache is cleared, as discussed above.
- Start up the Wireshark packet sniffer
- Enter the following URL into your browser http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file3.html
- Stop Wireshark packet capture, and enter “http” in the display-filter-specification window, so that only captured HTTP messages will be displayed.
实验结果
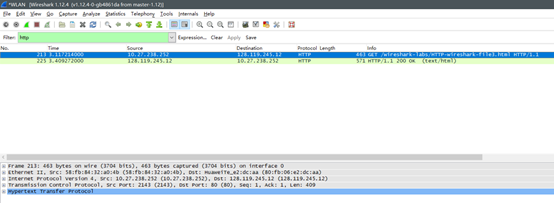
实验回答
How many HTTP GET request messages did your browser send? Which packet number in the trace contains the GET message for the Bill or Rights?
仅发送了一个GET

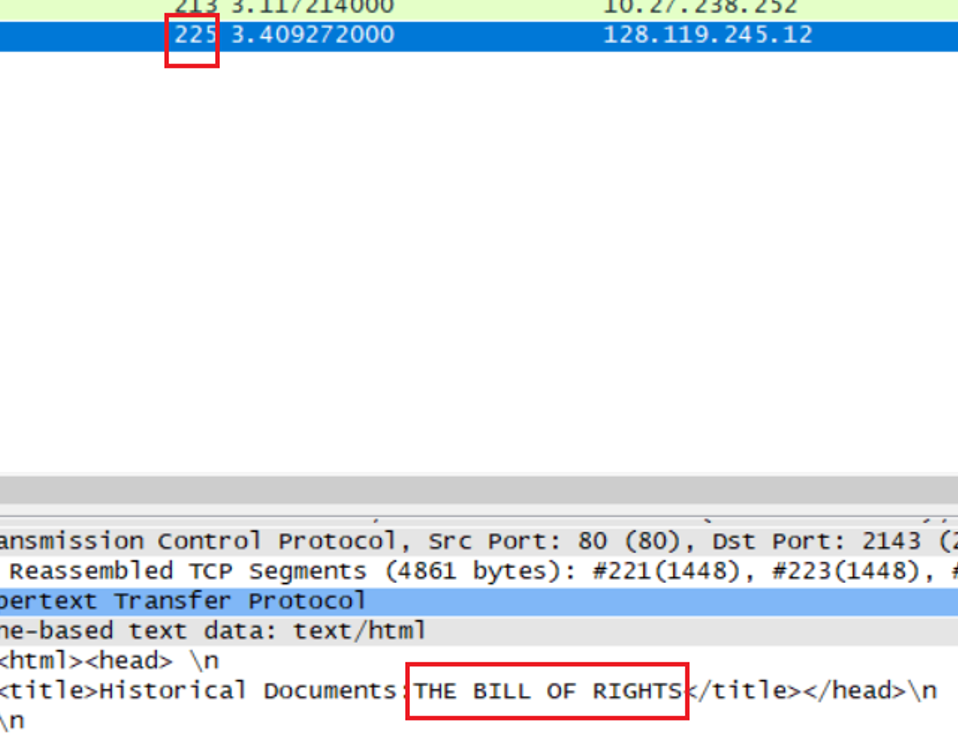
第225个中有“THE BILL OF RIGHTS”
Which packet number in the trace contains the status code and phrase associated with the response to the HTTP GET request?
同样是225返回了状态码200 OK

What is the statu code and phrase in the response?
同上一题,200 OK
How many data-containing TCP segments were needed to carry the single HTTP response and the text of the Bill
of Rights?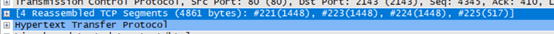
有4个TCP协议承载单个HTTP响应的权利法案的文本
HTML文本相当长,一个TCP数据包不能容纳,因此单个HTTP响应消息由TCP分成几个部分,每个部分包含在单独的TCP报文段中。
4.HTML Documents with Embedded Objects
步骤
- Start up your web browser, and make sure your browser’s cache is cleared, as discussed above.
- Start up the Wireshark packet sniffer
- Enter the following URL into your browser http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file4.html
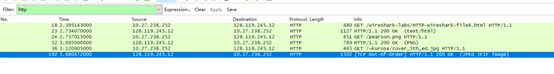
- Your browser should display a short HTML file with two images. These two images are referenced in the base HTML file. That is, the images themselves are not contained in the HTML; instead the URLs for the images are contained in the downloaded HTML file. As discussed in the textbook, your browser will have to retrieve these logos from the indicated web sites. Our publisher’s logo is retrieved from the www.aw-bc.com web site. The image of the cover for our 5th edition (one of our favorite covers) is stored at the manic.cs.umass.edu server.
- Stop Wireshark packet capture, and enter “http” in the display-filter-specification window, so that only captured HTTP messages will be displayed.
实验结果
问题回答
How many HTTP GET request messages did your browser send? To which Internet addresses were these GET
requests sent?发送了三个GET,都发送到了一个IP:128.119.245.12
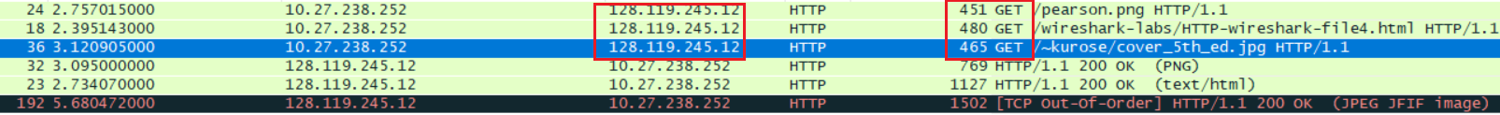
Can you tell whether your browser downloaded the two images serially, or whether they were downloaded from the two web sites in parallel? Explain.
不是同时给下载的,这些包都是先后发出的,有时间差。

需要注意的是:第二张图片出现了TCP Oou-of-order,查阅资料可得,同一台主机的数据包应该是连续的,当wireshark发现后一个包的Seq号小于前一个包的Seq Len时,就会认为是乱序了,因此提示 [TCP Out-of-Order]。产生的原因有很多,但是多半是网络拥塞,导致顺序包抵达时间不同,延时太长,或者包丢失,需要重新组合数据单元 因为他们可能是通过不同的路径到达你电脑上面的。
清理浏览器缓存后再次实验,未出现TCP Oou-of-order
TCP
TCP传输控制协议(Transmission Control Protocol),是一种面向连接的、可靠的、基于字节流的传输层中的通信协议。
研究TCP的几个方面:
- Capturing a bulk TCP transfer from your computer to a remote server
- A first look at the captured trace
- TCP Basics
- TCP congestion control in action
实验步骤及结果
1. Capturing a bulk TCP transfer from your computer to a remote server
步骤
- Start up your web browser. Go the http://gaia.cs.umass.edu/wireshark-labs/alice.txt and retrieve an ASCII copy of Alice in Wonderland. Store this file somewhere on your computer.
- Next go to http://gaia.cs.umass.edu/wireshark-labs/TCP-wireshark-file1.html.You should see a screen that looks like:
Use the Browse button in this form to enter the name of the file (full path name) on your computer containing Alice in Wonderland (or do so manually). Don’t yet press the “Upload alice.txt file” button. - Now start up Wireshark and begin packet capture (Capture->Start) and then press OK on the Wireshark Packet Capture Options screen (we’ll not need to select any options here).
- Returning to your browser, press the “Upload alice.txt file” button to upload the file to the gaia.cs.umass.edu server. Once the file has been uploaded, a short congratulations message will be displayed in your browser window.
- Stop Wireshark packet capture. Your Wireshark window should look similar to the window shown below.
实验结果
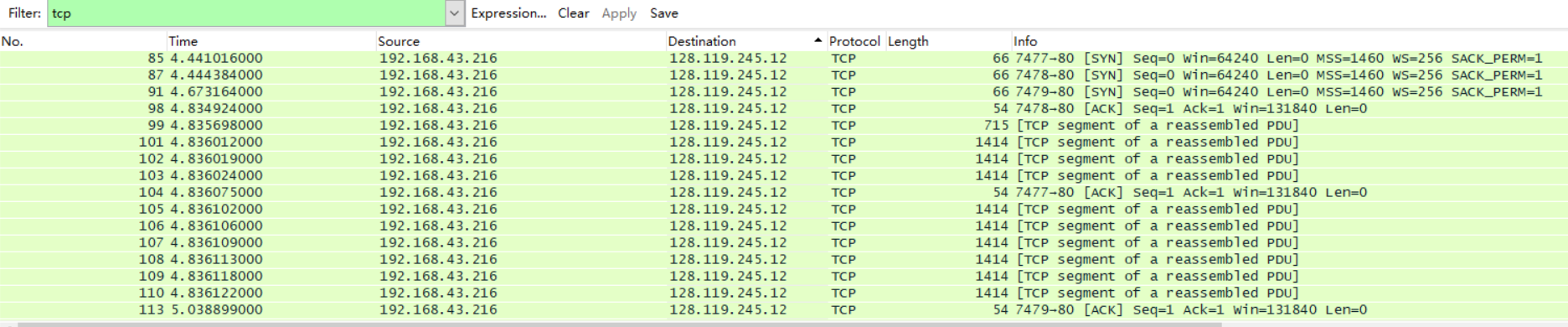
2. A first look at the captured trace
步骤
- First, filter the packets displayed in the Wireshark window by entering “tcp” (lowercase, no quotes, and don’t forget to press return after entering!) into the display filter specification window towards the top of the Wireshark window.
实验结果
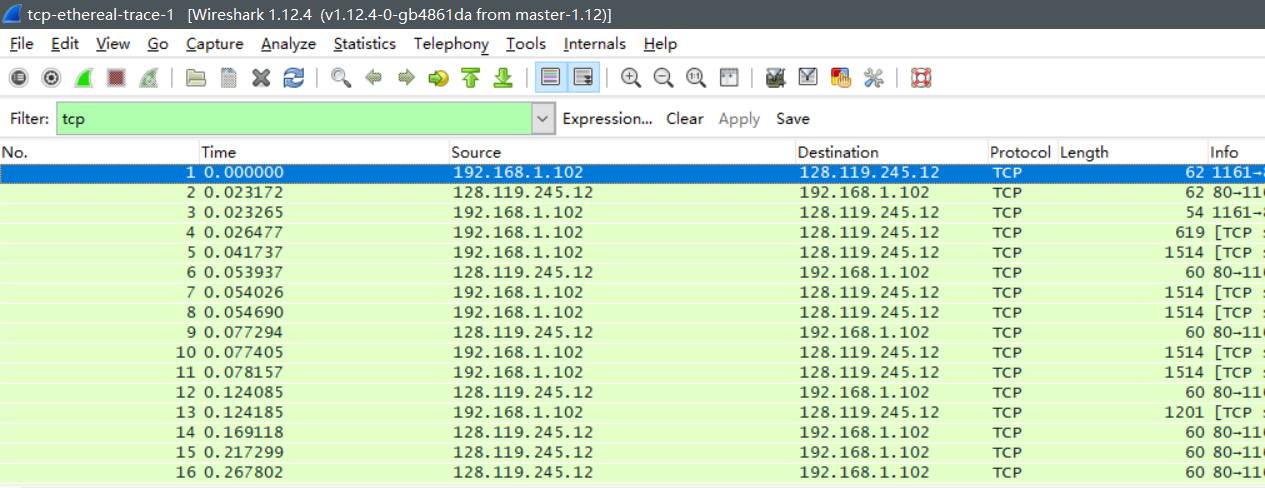
问题
What is the IP address and TCP port number used by the client computer (source) that is transferring the file to gaia.cs.umass.edu? To answer this question, it’s probably easiest to select an HTTP message and explore the details of the TCP packet used to carry this HTTP message, using the “details of the selected packet header window” (refer to Figure 2 in the “Getting Started with Wireshark” Lab if you’re uncertain about the Wireshark windows.
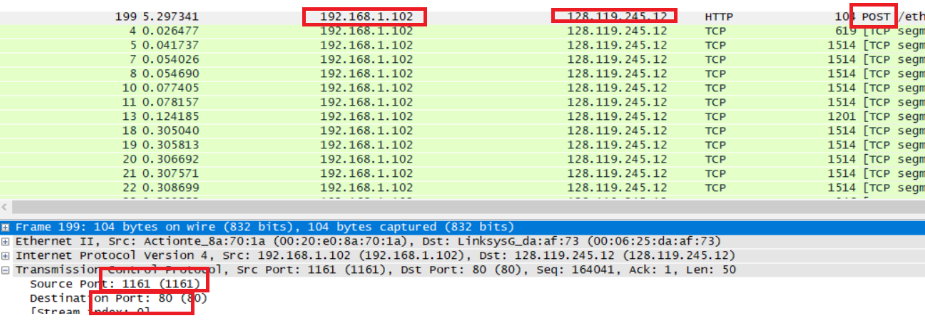
通过找到post内容,可以发现客户端计算机的IP为192.168.1.102,端口为1161
What is the IP address of gaia.cs.umass.edu? On what port number is it sending and receiving TCP segments for this connection?
同上题,可知gaia.cs.umass.edu的IP为128.119.245.12,端口为80
What is the IP address and TCP port number used by your client computer (source) to transfer the file to gaia.cs.umass.edu?
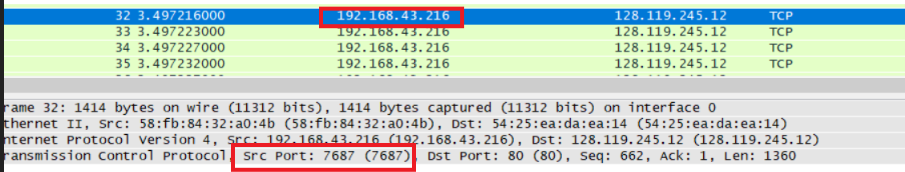
自己的IP是192.168.43.216,端口为7687
3. TCP Basics
问题
What is the sequence number of the TCP SYN segment that is used to initiate the TCP connection between the client computer and gaia.cs.umass.edu? What is it in the segment that identifies the segment as a SYN segment?
首先先学习三次握手的过程:
第一次握手:建立连接时,客户端发送syn包(syn=j)到服务器,并进入SYN_SENT状态,等待服务器确认;SYN:同步序列编号(Synchronize Sequence Numbers)。
第二次握手:服务器收到syn包,必须确认客户的SYN(ack=j+1),同时自己也发送一个SYN包(seq=k),即SYN+ACK包,此时服务器进入SYN_RECV状态
第三次握手:客户端收到服务器的SYN+ACK包,向服务器发送确认包ACK(ack=k+1),此包发送完毕,客户端和服务器进入ESTABLISHED(TCP连接成功)状态,完成三次握手。

SYN的序号为0
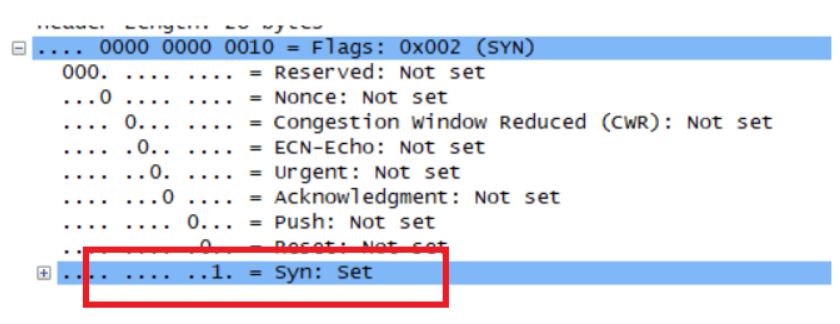
把其中Flag中的Syn置为1
What is the sequence number of the SYNACK segment sent by gaia.cs.umass.edu to the client computer in reply to the SYN? What is the value of the Acknowledgement field in the SYNACK segment? How did gaia.cs.umass.edu determine that value? What is it in the segment that identifies the segment as a SYNACK segment?
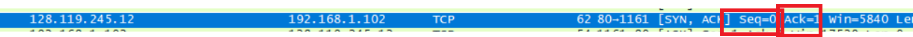
SYN的序号为0,Ack=1,ack是根据上一次客户端发送的Seq+1所得到的
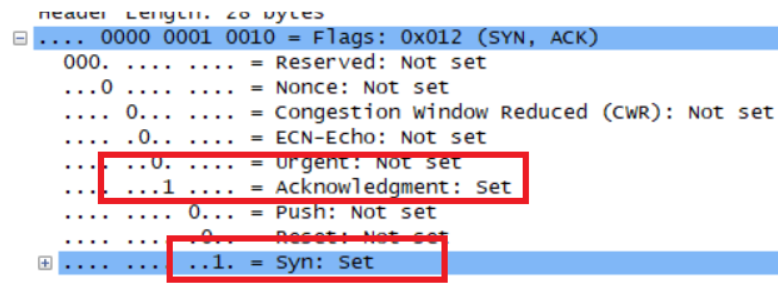
将Syn和Acknowledgement置为1
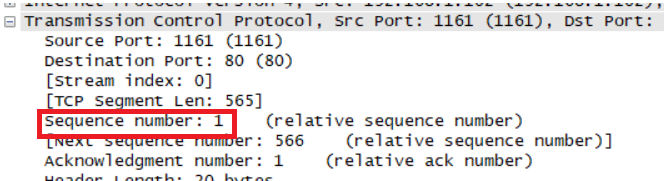
What is the sequence number of the TCP segment containing the HTTP POST command? Note that in order to find the POST command, you’ll need to dig into the packet content field at the bottom of the Wireshark window, looking for a segment with a “POST” within its DATA field.
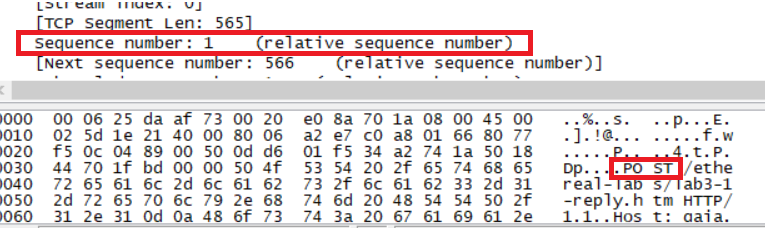
seq = 1
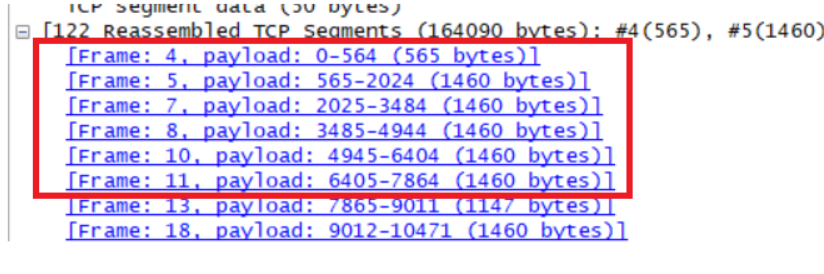
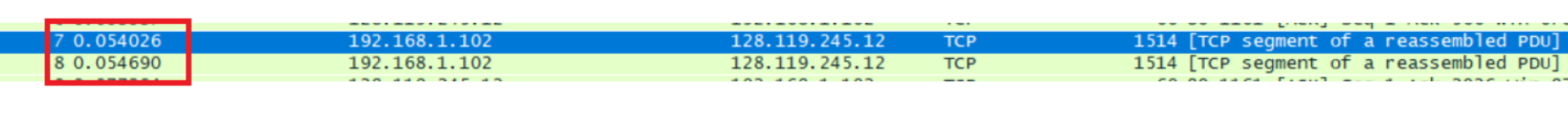
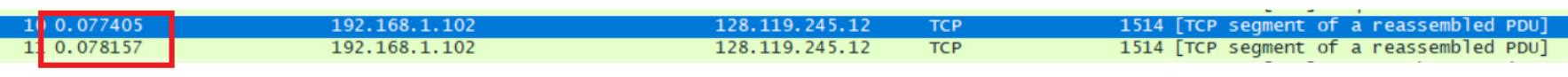
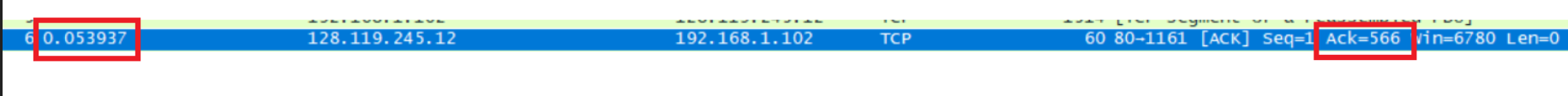
Consider the TCP segment containing the HTTP POST as the first segment in the TCP connection. What are the sequence numbers of the first six segments in the TCP connection (including the segment containing the HTTP POST)? At what time was each segment sent? When was the ACK for each segment received? Given the difference between when each TCP segment was sent, and when its acknowledgement was received, what is the RTT value for each of the six segments? What is the EstimatedRTT value (see Section 3.5.3, page 239 in text) after the receipt of each ACK? Assume that the value of the EstimatedRTT is equal to the measured RTT for the first segment, and then is computed using the EstimatedRTT equation on page 239 for all subsequent segments.
Segment 1 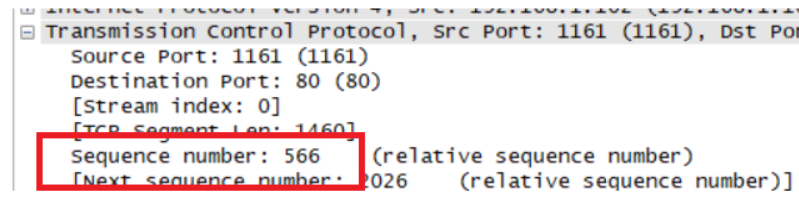
Segment 2 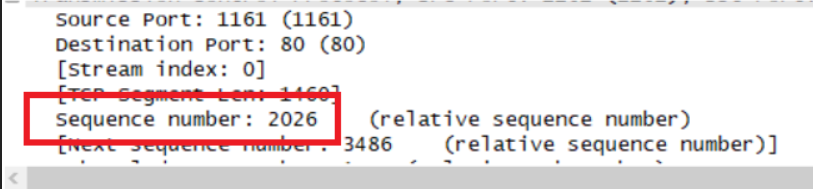
Segment 3 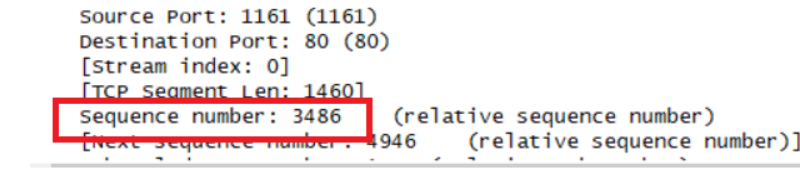
Segment 4 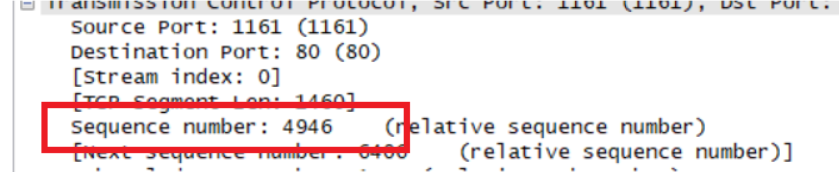
Segment 5 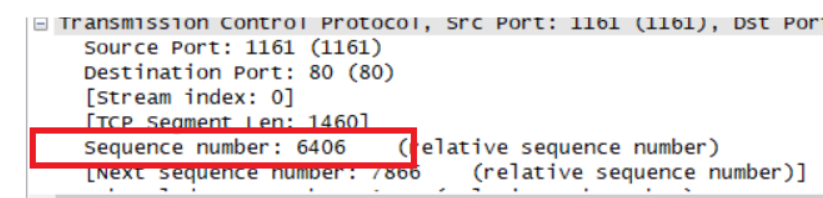
Segment 6 
![1561773435301].\sources\1561773435301.png)
Sqe Sent time Ack time RTT EstimatedRTT Length/bytes Segment 1 1 0.026477 0.053937 0.02746 0.02746 565 Segment 2 566 0.041737 0.077294 0.035557 0.028472 1460 Segment 3 2026 0.054026 0.124086 0.070059 0.033670 1460 Segment 4 3486 0.054690 0.169118 0.11443 0.043765 1460 Segment 5 4946 0.077405 0.217299 0.13989 0.055781 1460 Segment 6 6406 0.078157 0.267802 0.18964 0.072513 1460 EstimatedRTT = 0.875 * Last EstimatedRTT + 0.125 * sample RTT EstimatedRTT定义是计算机网络中TCP协议对下一个数据往返值进行的估计,并利用此估计值来判断数据超时时间。即维护一个SampleRTT的均值,一旦获得新的SampleRTT,会更新EstimatedRTT,除此之外,还要测量RTT的变化,定义DevRTT,用于估算SampleRTT 偏离EstimatedRTT的程度:DevRTT=(1-b) * DevRTT+b * |SampleRTT-EstimatedRTT|,b的值一般为0.25。当我们得到EstimatedRTT和DevRTT,即可设置TCP超时间隔:TimeoutInterval (RTO) = EstimatedRTT+4*DevRTT
What is the length of each of the first six TCP segments?
见第七题表格。
What is the minimum amount of available buffer space advertised at the received for the entire trace? Does the lack of receiver buffer space ever throttle the sender?
对于整个跟踪包,最小的窗口是5480

TCP Window Size ,双方的可用的缓冲区大小,若一方通知 window=0 ,另一端将不再发送数据,但会定时询问是否缓冲区是否可用,若不可用,则重置时间继续等待,若可用再发送。一般是 2 Byte=65535Bit
Are there any retransmitted segments in the trace file? What did you check for (in the trace) in order to answer this question?
没有发现重传的情况,因为序列号一直在增大,通过检查TCP Segments中的sequence number
How much data does the receiver typically acknowledge in an ACK? Can you identify cases where the receiver
is ACKing every other received segment (see Table 3.2 on page 247 in the text).通过第七题可知,在两个ACK之间传送1460bytes,每隔一个接收到的区段之间的数据相隔1460*2=2920的bytes
What is the throughput (bytes transferred per unit time) for the TCP connection? Explain how you calculated this value.
发送整个过程是从4到202
总数据量为 164091 - 1 = 164090bytes
总时间为 5.455830 - 0.026477 = 5.4294sec
164090bytes / 5.4294sec = 30.222 KBytes/sec

4.TCP congestion control in action
步骤
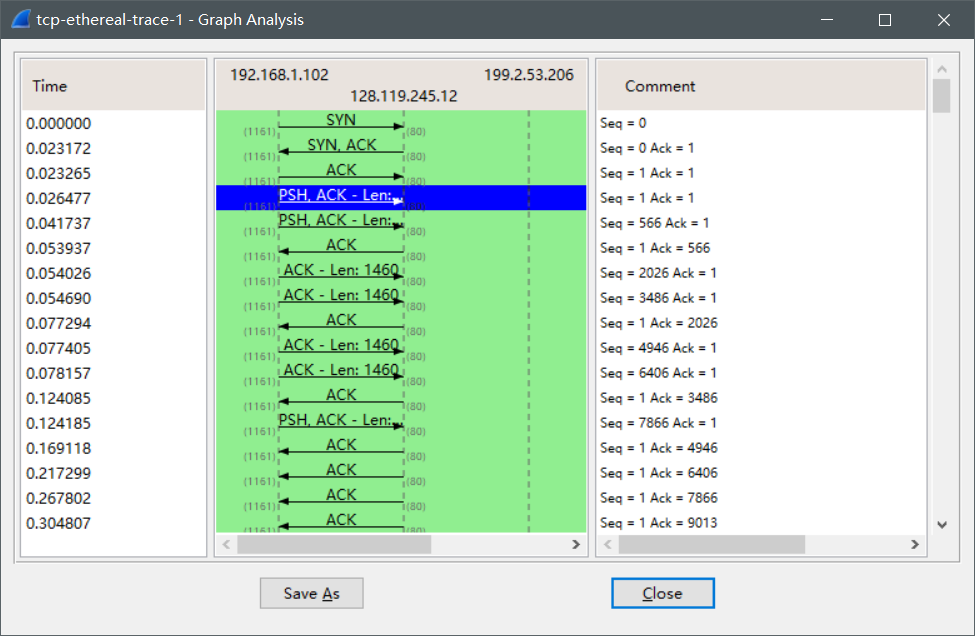
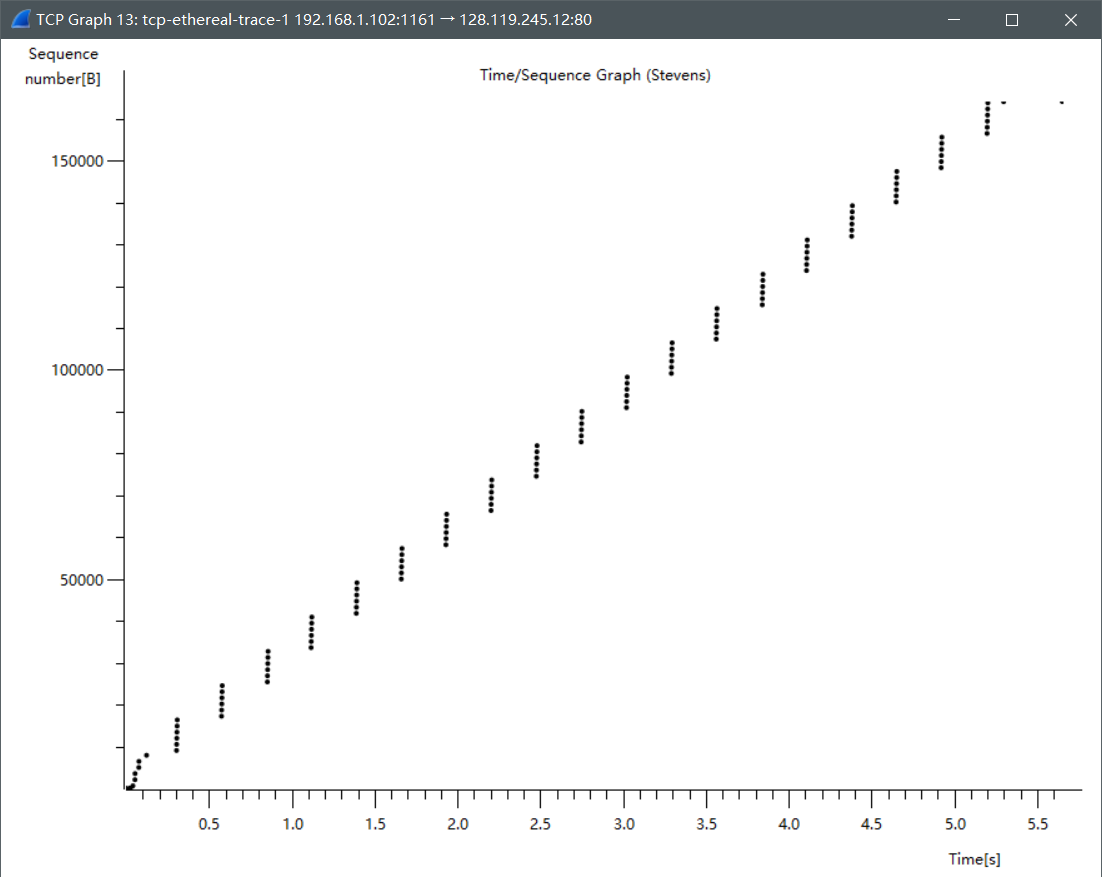
- Select a TCP segment in the Wireshark’s “listing of captured-packets” window. Then select the menu : Statistics->TCP Stream Graph-> Time-Sequence-Graph(Stevens). You should see a plot that looks similar to the following
plot, which was created from the captured packets in the packet trace tcp-ethereal-trace-1 in http://gaia.cs.umass.edu/wireshark-labs/wireshark-traces.zip (see earlier footnote ):
问题
Use the Time-Sequence-Graph(Stevens) plotting tool to view the sequence number versus time plot of segments being sent from the client to the gaia.cs.umass.edu server. Can you identify where TCP’s slowstart phase begins and ends, and where congestion avoidance takes over? Comment on ways in which the measured data differs from the idealized behavior of TCP that we’ve studied in the text.

我们可以看出慢启动在刚开始的地方,但是从这个图里看不出慢启动结束和拥塞避免的地方。
Answer each of two questions above for the trace that you have gathered when you transferred a file from your computer to gaia.cs.umass.edu
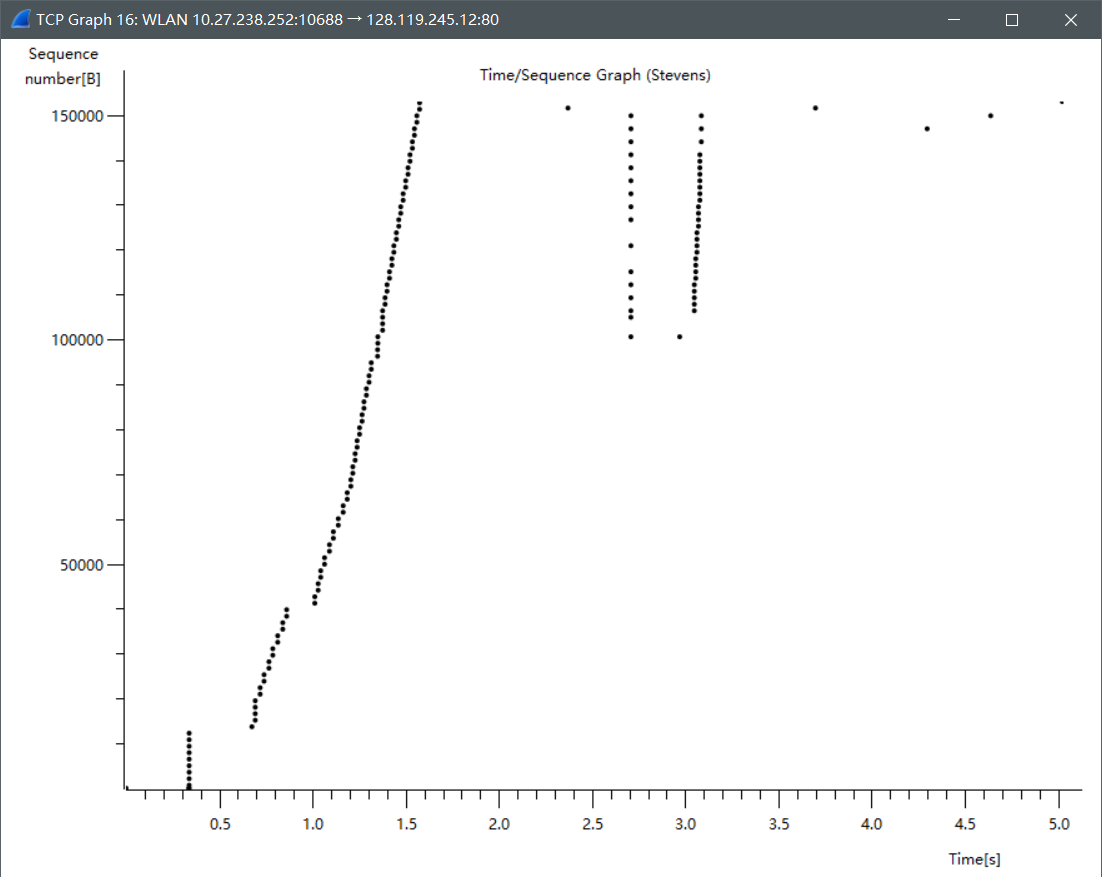
同上一题结果,慢启动在刚开始的时候出现。
ICMP
ICMP控制报文协议(Internet Control Message Protocol),是TCO/IP协议簇的一个子协议,用于在IP主机、路由器之间传递控制消息。
研究ICMP相关内容
- ICMP messages generating by the Ping program;
- ICMP messages generated by the Traceroute program;
- the format and contents of an ICMP message.
实验步骤及结果
ICMP and Ping
步骤
- Let’s begin this adventure by opening the Windows Command Prompt application (which
can be found in your Accessories folder). - Start up the Wireshark packet sniffer, and begin Wireshark packet capture.
- The ping command is in c:\windows\system32, so type either “ping –n 10 hostname” or “c:\windows\system32\ping –n 10 hostname” in the MS-DOS command line (without quotation marks), where hostname is a host on another continent. If you’re outside of Asia, you may want to enter www.ust.hk for the Web server at Hong Kong University of Science and Technology. The argument “-n 10” indicates that 10 ping messages should be sent. Then run the Ping program by typing return.
- When the Ping program terminates, stop the packet capture in Wireshark.
实验结果
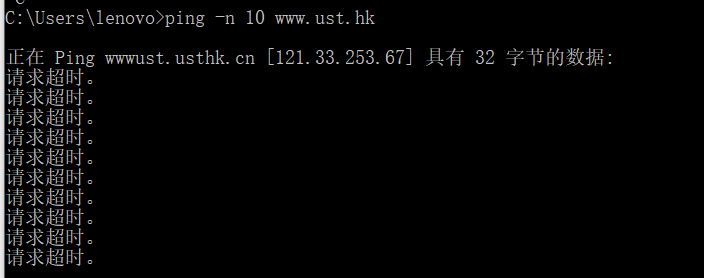
请求超时
访问必应网站
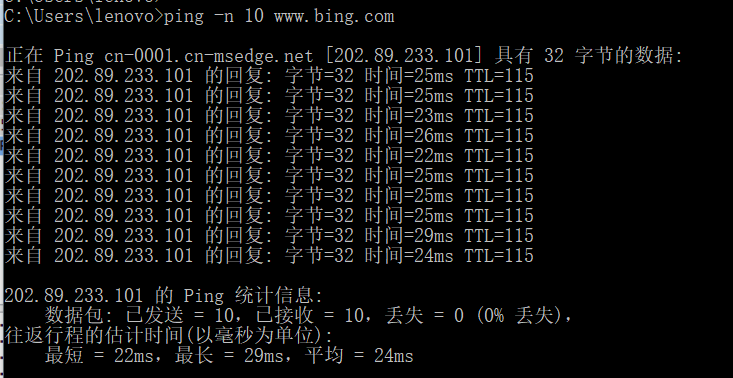
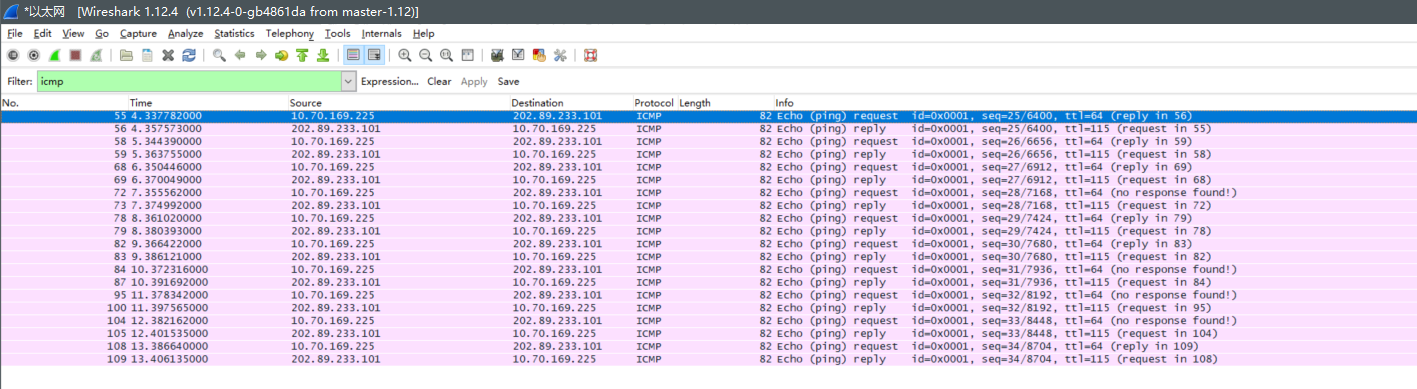
问题回答
What is the IP address of your host? What is the IP address of the destination host?
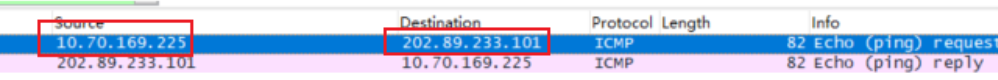
我的IP 为10.70.169.225
服务器的IP为202.89.233.101Why is it that an ICMP packet does not have source and destination port numbers?
ICMP的学习:ICMP(Internet Control Message Protocol)Internet控制报文协议。它是TCP/IP协议簇的一个子协议,用于在IP主机、路由器之间传递控制消息。控制消息是指网络通不通、主机是否可达、路由是否可用等网络本身的消息。这些控制消息虽然并不传输用户数据,但是对于用户数据的传递起着重要的作用。
ICMP是网络层的协议,不需要TCP和UDP承载,直接使用IP报承载,因此不需要源端口号和目的端口号,只需要目的地址即可。
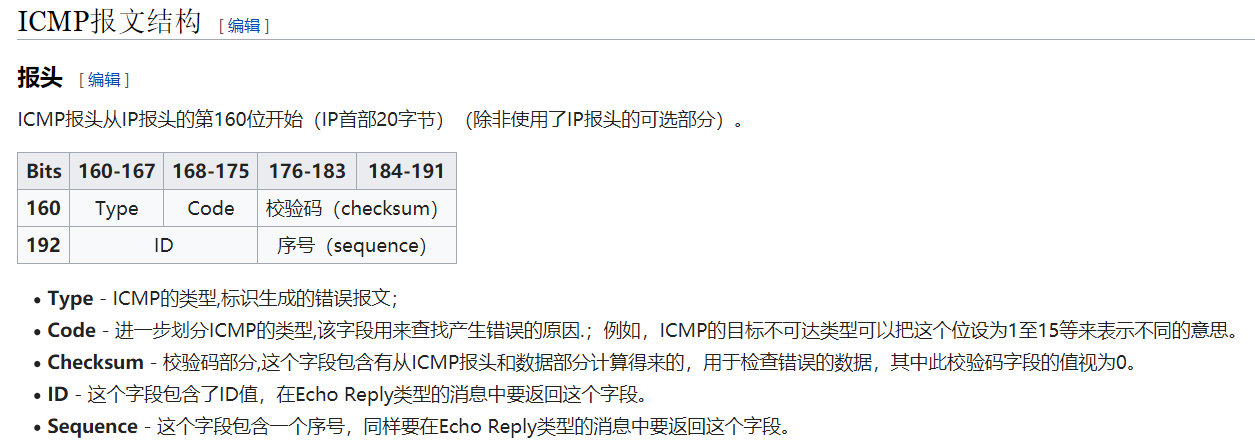
Examine one of the ping request packets sent by your host. What are the ICMP type and code numbers? What other fields does this ICMP packet have? How many bytes are the checksum, sequence number and identifier
fields?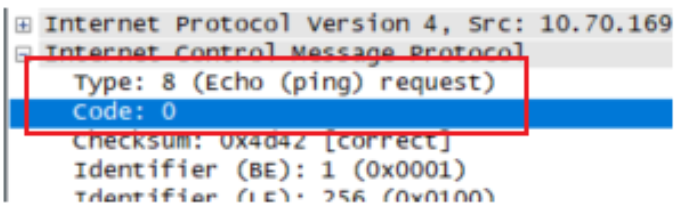
Type 是8,Code是0
还有校验码(checksum),ID,序号(sequence)
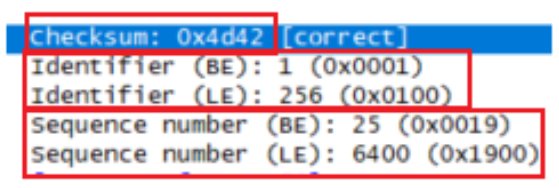
都是16位,2个字节。
需要注意是:发现有BE和LE的不同情况,查询wireshark官网中After I discovered that the Windows ping sends ICMP echo request packets with the sequence number in little-endian byte order, but the Linux ping sends it in proper big-endian format, a discussion about it took place on the mailing list as to how to handle it (refer to http://www.wireshark.org/lists/wireshark-dev/200909/msg00216.html). However,to keep things simple and avoid adding any new ICMP preferences and/or trying to guess at the byte order, I thought why not just display the sequence number in both formats, so that’s what this patch does.”
目的是考虑到Windows和Linux系统发出的ping报文的字节顺序不一样,(windows为LE:little-endian byte order,Linux为BE:big-endian)。
查询维基百科中ICMP报文结构可得
Examine the corresponding ping reply packet. What are the ICMP type and code numbers?
What other fields does this ICMP packet have? How many bytes are the
checksum, sequence number and identifier fields?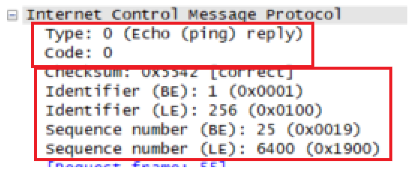
Type是0,Code是0,其中Checksum,ID,Seq都是16位,2个字节
学习常用的ICMP报文类型
CMP提供多种类型的消息为源端节点提供网络层的故障信息反馈,它的报文类型可以归纳为以下5个大类: 诊断报文(类型8,代码0;类型0,代码0); 目的不可达报文(类型3,代码0-15); 重定向报文(类型5,代码0-4); 超时报文(类型11,代码0-1); 信息报文(类型12-18)。
ICMP and Traceroute
步骤
- Let’s begin by opening the Windows Command Prompt application (which can be found in your Accessories folder).
- Start up the Wireshark packet sniffer, and begin Wireshark packet capture.
- The tracert command is in c:\windows\system32, so type either “tracert hostname” or “c:\windows\system32\tracert
hostname” in the MS-DOS command line (without quotation marks), where hostname is a host on another continent. (Note that on a Windows machine, the command is “tracert” and not “traceroute”.) If you’re outside of Europe, you may want to enter www.inria.fr for the Web server at INRIA, a computer science research institute in France. Then run the Traceroute program by typing return. - When the Traceroute program terminates, stop packet capture in Wireshark. When the Traceroute program terminates, stop packet capture in Wireshark.
实验结果
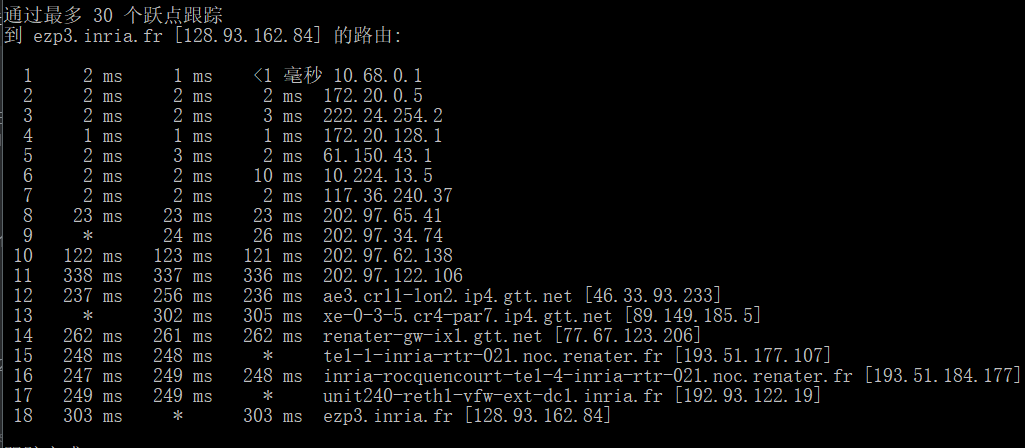
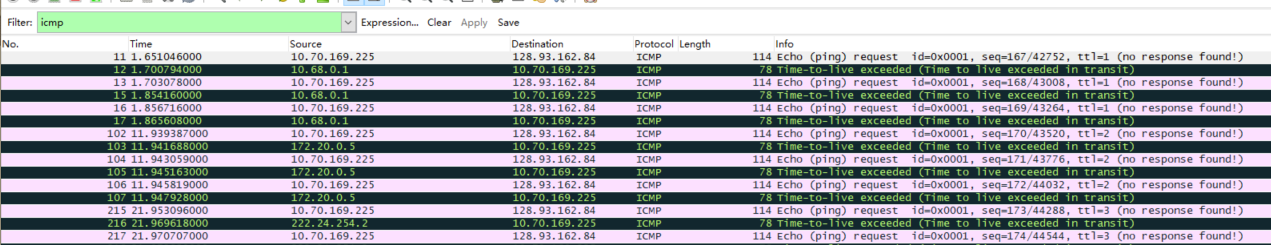
问题回答
What is the IP address of your host? What is the IP address of the target destination host?
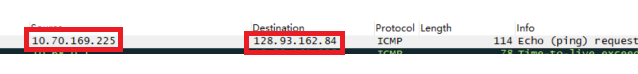
我的IP地址为10.70.169.225
服务器的IP地址为128.93.162.84
If ICMP sent UDP packets instead (as in Unix/Linux), would the IP protocol number still be 01 for the probe packets? If not, what would it be?
如果在ICMP发生UDP数据报,IP协议号应该为0x11,十进制为17,表示交给UDP
Examine the ICMP echo packet in your screenshot. Is this different from the ICMP ping query packets in the first half of this lab? If yes, how so?
tracert相关部分学习:Tracert(跟踪路由)是路由跟踪实用程序,用于确定 IP 数据报访问目标所采取的路径。Tracert 该诊断实用程序将包含不同生存时间 (TTL) 值的 Internet 控制消息协议(ICMP) 回显数据包发送到目标,以决定到达目标采用的路由。要在转发数据包上的 TTL 之前至少递减 1,必需路径上的每个路由器,所以 TTL 是有效的跃点计数。
因此返回的都是Time-to-live(TTL)
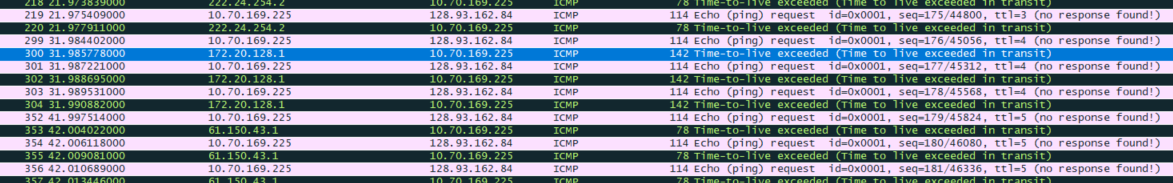
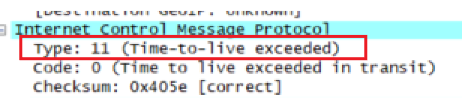
所以Type不一样,Code等于0是一样的,checksum是不会一样的,同时不存在ID和Seq了。
而最后的ICMP响应数据包中非超时的ICMP的Type也为0是一样的,这里checksum和ID以及Seq可能会不一样,
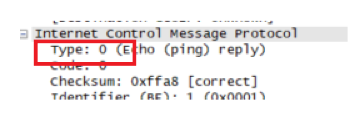
Examine the ICMP error packet in your screenshot. It has more fields than the ICMP echo packet. What is included in those fields?
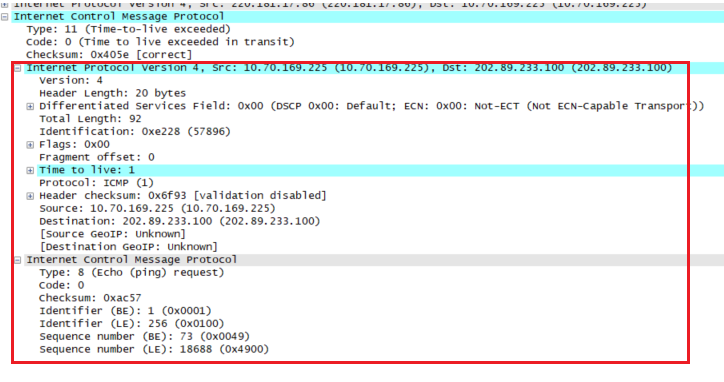
多了ICMP请求数据包中的内容。
查询相关资料可得:当TTL值变成0时,不能够继续传送,路由器就回复了一个ICMP相应,这个数据包类型是11,代码是0,需要注意的是,在ICMP的结尾部分包含了原echo请求的IP头和ICMP数据的拷贝。因此这个数据包也被叫做ICMP双头包,表示包含有两个ICMP的包头信息。这样做的目的是在网络故障检修的时候会非常有用。Examine the last three ICMP packets received by the source host. How are these packets different from the ICMP error packets? Why are they different?
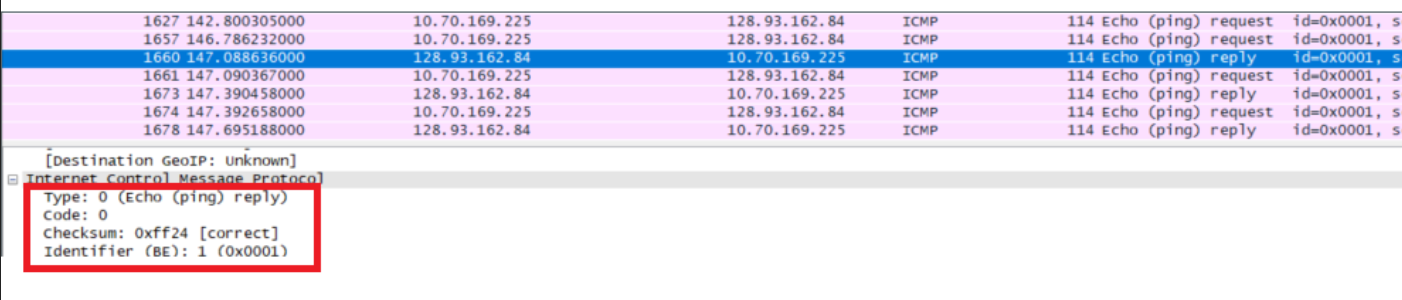
最后的三个ICMP相应数据包是目的主机发送给我的ICMP回应数据包,因为这是TTL已经足够大,可以到达最终服务器,因此不会被丢弃,返回正常的Type 0 Code 0 的reply的ICMP数据包。
而超时的数据包会返回Type 11 Code 0 以及ICMP请求的部分
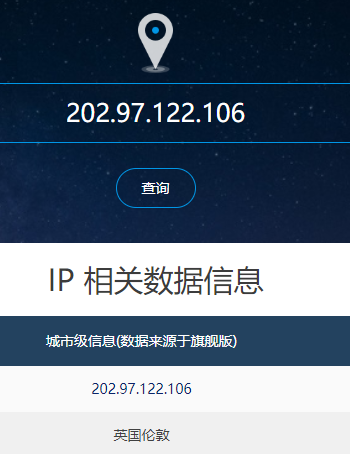
Within the tracert measuremenzu’houts, is there a link whose delay is significantly longer than others? Refer to the screenshot in Figure 4, is there a link whose delay is significantly longer than others? On the basis of the router
names, can you guess the location of the two routers on the end of this link?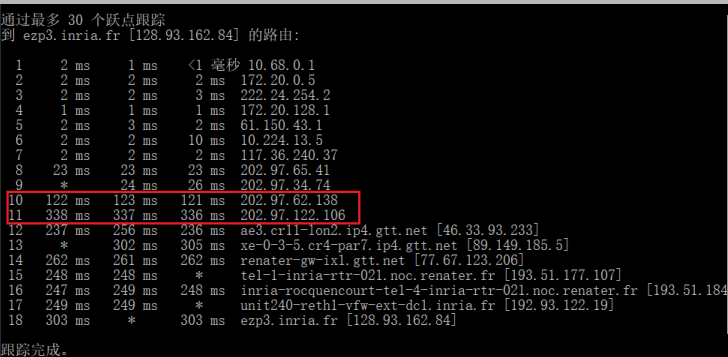
根据图中的截图可以发现第10个到11个节点的延迟突然增加,可能是过 太平洋电缆/光缆到法国那边
经过查询IP地址可得
第10个IP202.97.62.138为北京
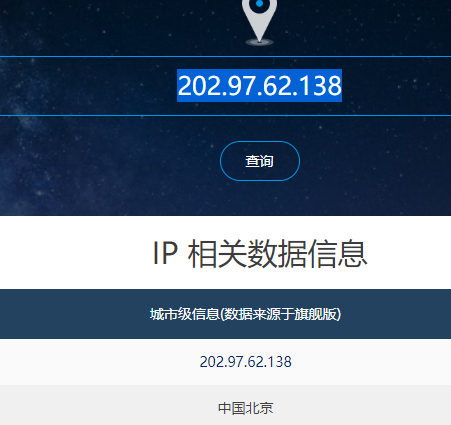
第11个IP202.97.122.106为英国伦敦
ARP
ARP地址解析协议(Address Resolution Protocol),是根据IP地址获得物理地址的一个TCP/IP协议。主机发送消息时将包含目标IP地址的ARP请求广播到局域网络上的所有主机,并接受返回消息,以此确定目标的物理地址。
研究ARP协议的几个方面:
- Capturing and analyzing Ethernet frames
实验步骤及结果
1.Capturing and analyzing Ethernet frames
步骤
- First, make sure your browser’s cache is empty. To do this under Mozilla Firefox V3, select Tools->Clear Recent History and check the box for Cache. For Internet Explorer, select Tools->Internet Options->Delete Files. Start up the Wireshark packet sniffer
- Enter the following URL into your browser http://gaia.cs.umass.edu/wireshark-labs/HTTP-ethereal-lab-file3.html Your
browser should display the rather lengthy US Bill of Rights. - Stop Wireshark packet capture. First, find the packet numbers (the leftmost column in the upper Wireshark window) of the HTTP GET message that was sent from your computer to gaia.cs.umass.edu, as well as the beginning of the HTTP response message sent to your computer by gaia.cs.umass.edu. You should see a screen that looks something like this (where packet 4 in the screen shot below contains the HTTP GET message)
- •Since this lab is about Ethernet and ARP, we’re not interested in IP or higher-layer protocols. So let’s change Wireshark’s “listing of captured packets” window so that it shows information only about protocols below IP. To have Wireshark do this, select Analyze->Enabled Protocols. Then uncheck the IP box and select OK. You should now see an Wireshark window that looks like:
实验结果
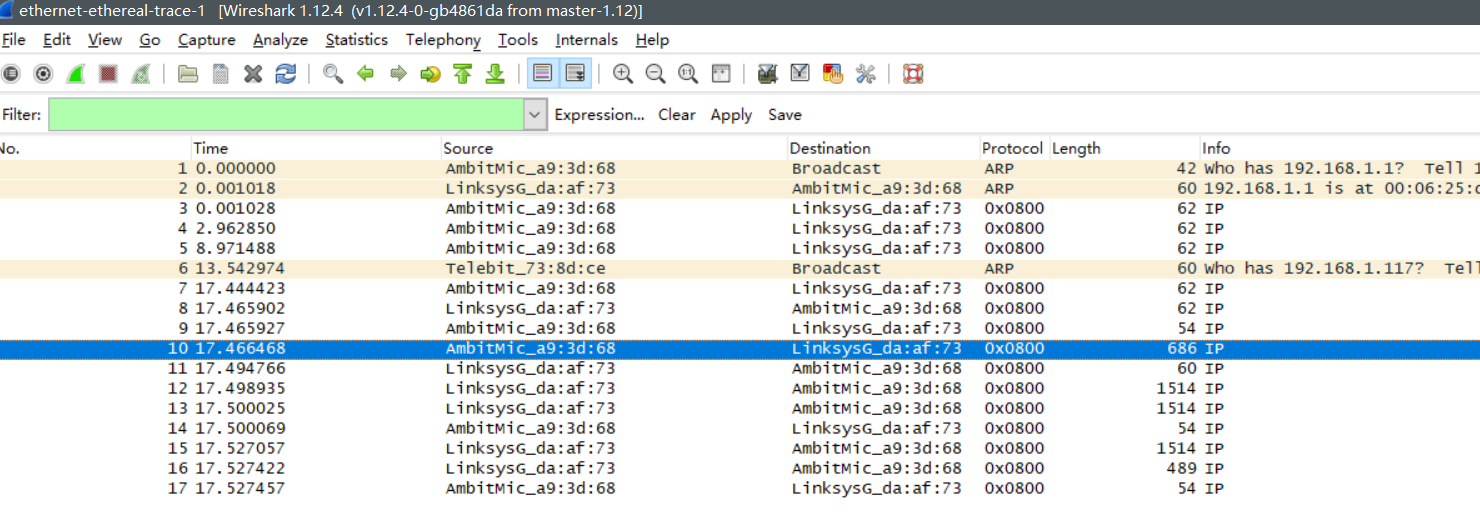
采用作者的抓包结果
问题回答
What is the 48-bit Ethernet address of your computer?
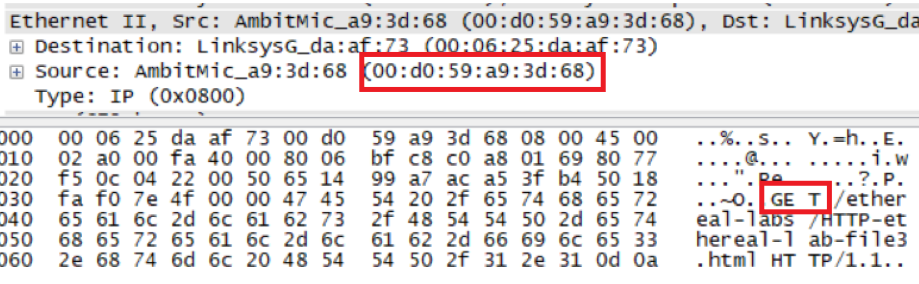
地址是00:d0:59:a9:3d:68
What is the 48-bit destination address in the Ethernet frame? Is this the Ethernet address of gaia.cs.umass.edu? (Hint: the answer is no). What device has this as its Ethernet address? [Note: this is an important question, and one that students sometimes get wrong. Re-read pages 468-469 in the text and make sure you understand the answer here.]
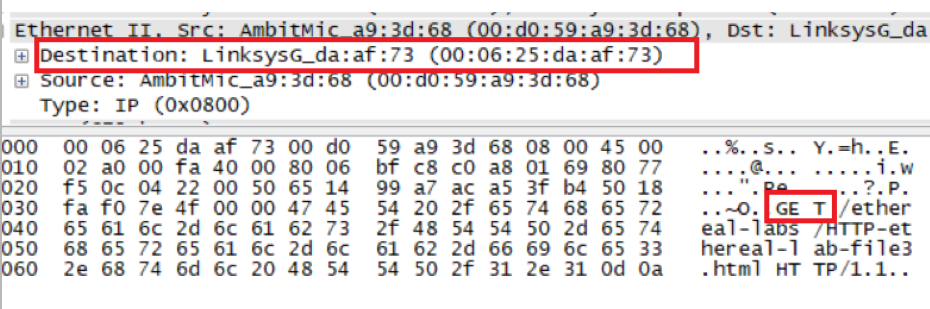
地址为00:06:25:da:af:73
不是gaia.cs.umass.edu的地址,因为这只是选择下一步转发的路由地址,不会是最终的地址
Give the hexadecimal value for the two-byte Frame type field. What upper layer protocol does this correspond to?
0x0800代表上层协议是IPv4
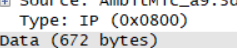
How many bytes from the very start of the Ethernet frame does the ASCII “G” in “GET” appear in the Ethernet frame?
每两个十六进制字符代表一个字节(8比特),则有16+16+16+7=55个Bytes
What is the value of the Ethernet source address? Is this the address of your computer, or of gaia.cs.umass.edu (Hint: the answer is no). What device has this as its Ethernet address?
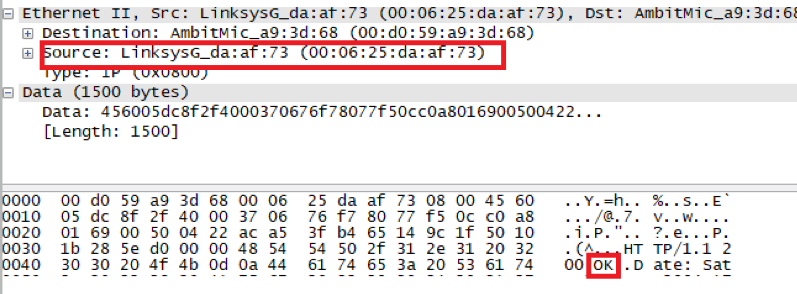
源地址为00:06:25:da:af:73
拥有这个以太网地址的设备是离我电脑最近的路由器,而不是gaia.cs.umass.edu的地址。
What is the destination address in the Ethernet frame? Is this the Ethernet address of your computer?
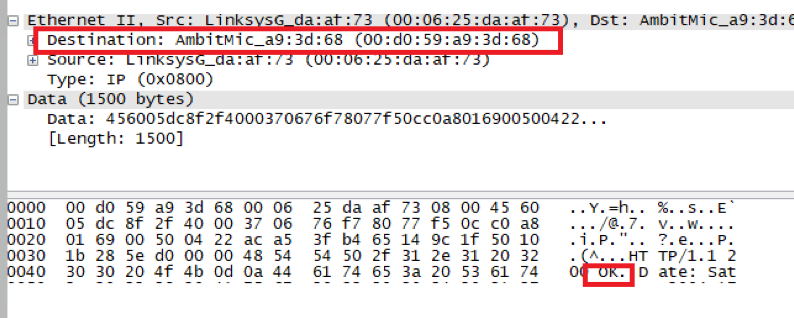
目的地址是00:d0:59:a9:3d:68
是我(作者)的以太网的地址
Give the hexadecimal value for the two-byte Frame type field. What upper layer protocol does this correspond to?
同样是0x0800,是IPv4
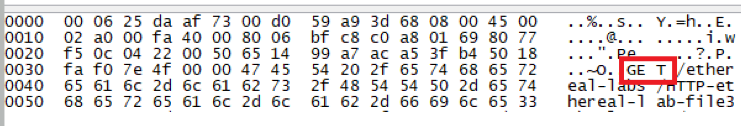
How many bytes from the very start of the Ethernet frame does the ASCII “O” in “OK” (i.e., the HTTP response code) appear in the Ethernet frame?
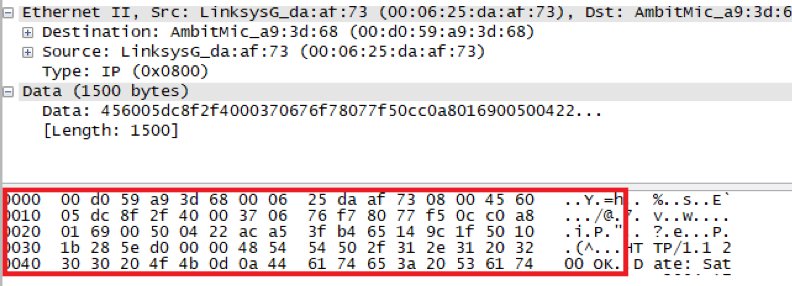
4*16+4 = 68Bytes
2.The Address Resolution Protocol
步骤
- MS-DOS. The arp command is in c:\windows\system32, so type either “arp” or “c:\windows\system32\arp” in the MS-DOS command line (without quotation marks). MS-DOS:arp命令位于 c:\windows\system32 中,因此在 MS-DOS命令行中 输入“arp”或“c:\windows\system32\arp”(没有引号)
问题解答
Write down the contents of your computer’s ARP cache. What is the meaning of each column value?
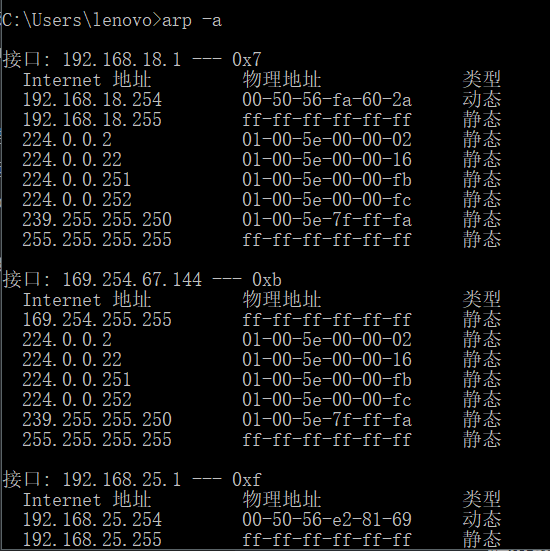
不同的接口代表不同的网卡,有不同的IP和MAC,类型分为动态和静态
步骤
- Clear your ARP cache, as described above.
- Next, make sure your browser’s cache is empty. To do this under Mozilla Firefox V3, select Tools->Clear Recent History and check the box for Cache. For Internet Explorer, select Tools->Internet Options->Delete Files
- Start up the Wireshark packet sniffer
- Enter the following URL into your browser http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-lab-file3.html Your browser should again display the rather lengthy US Bill of Rights.
- Stop Wireshark packet capture. Again, we’re not interested in IP or higher-layer protocols, so change Wireshark’s “listing of captured packets” window so that it shows information only about protocols below IP. To have Wireshark do this, select Analyze->Enabled Protocols. Then uncheck the IP box and select OK. You should now see an Wireshark window that looks like:
问题解答
What are the hexadecimal values for the source and destination addresses in the Ethernet frame containing the ARP request message?
由于我目前没有无限路由器(无法抓取ARP广播),直接分析作者抓包情况
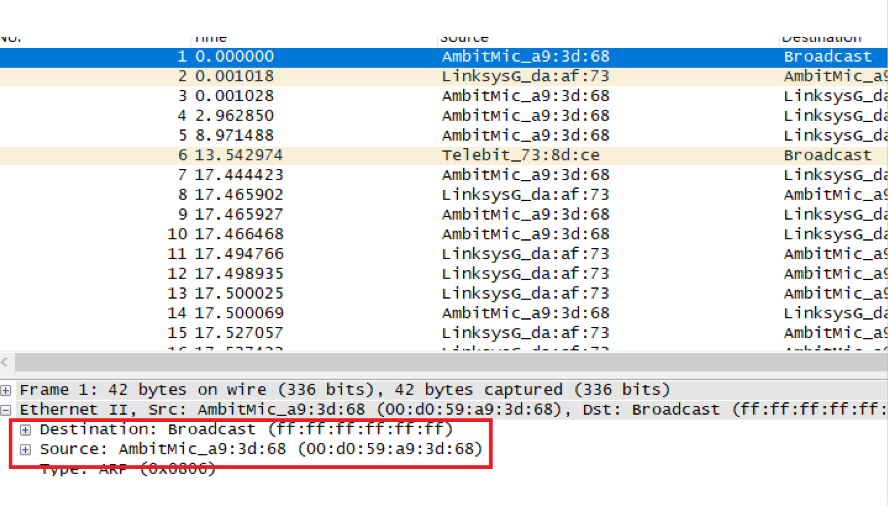
源地址:00:d0:59;a9:3d:68
目的地址:ff:ff:ff:ff:ff:ff
Give the hexadecimal value for the two-byte Ethernet Frame type field. What upper layer protocol does this
correspond to?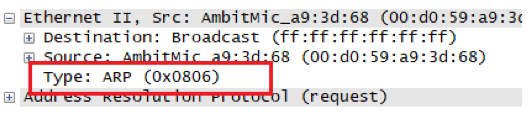
0x0806为ARP
Download the ARP specification from ftp://ftp.rfc-editor.org/in-notes/std/std37.txt. A readable, detailed
discussion of ARP is also at http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/arp.html.a)How many bytes from the very beginning of the Ethernet frame does the ARP opcode field begin?
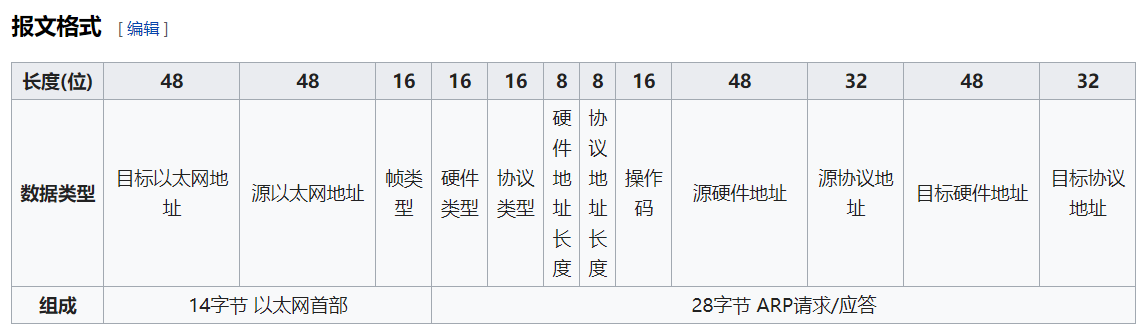
维基百科中报文格式可知,操作码为第21个字节
b)What is the value of the opcode field within the ARP-payload part of the Ethernet frame in which an ARP request is made?
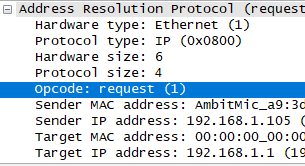
操作码为1
查询资料可得:1为ARP请求,2为ARP应答,3为RARP请求,4为RARP应答。
c)Does the ARP message contain the IP address of the sender?
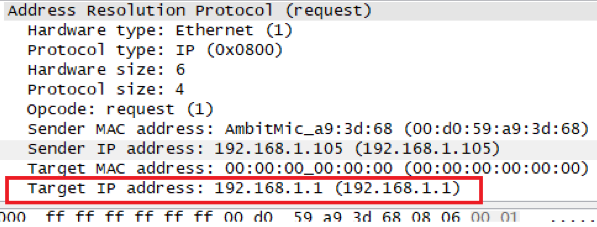
为192.168.1.1
d)Where in the ARP request does the “question” appear – the Ethernet address of the machine whose corresponding IP address is being queried?
同上题图,以太网地址全为0,请求是广播。
Now find the ARP reply that was sent in response to the ARP request.
a)How many bytes from the very beginning of the Ethernet frame does the ARP opcode field begin?同12a),结果也为Bytes
b)What is the value of the opcode field within the ARP-payload part of the Ethernet frame in which an ARP response is made?
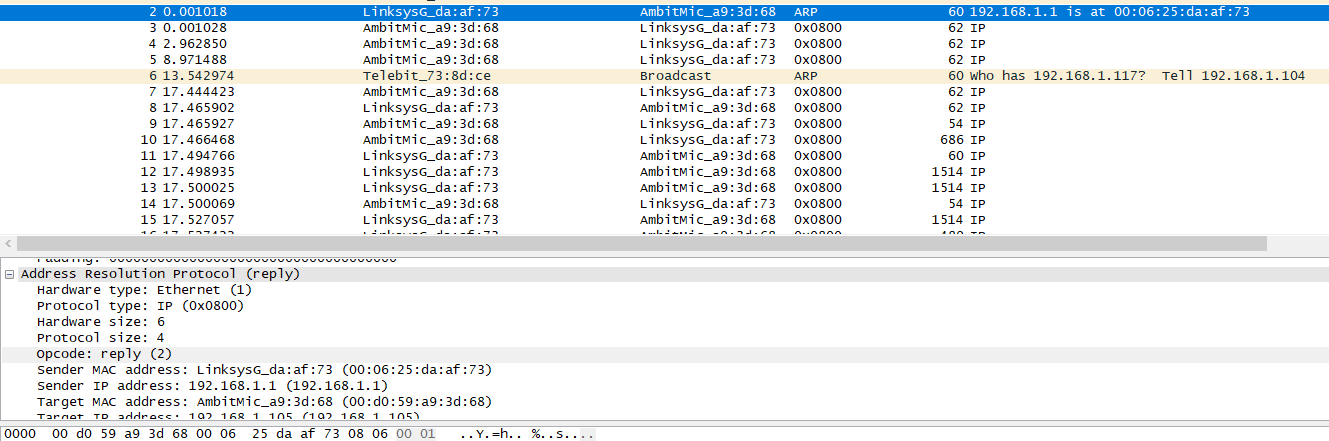
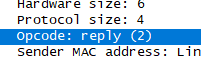
结果为2
c)Where in the ARP message does the “answer” to the earlier ARP request appear – the IP address of the machine having the Ethernet address whose corresponding IP address is being queried?
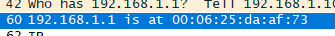
请求的答案中IP为192.168.1.1 MAC为00:06:25:da:af:73
What are the hexadecimal values for the source and destination addresses in the Ethernet frame containing the
ARP reply message?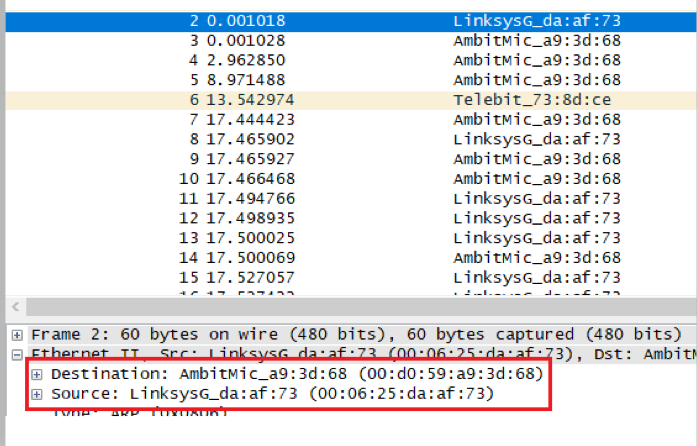
源地址为00:06:25:da:af:73 , 目的为00:d0:59:a9:3d:68
Open the ethernet-ethereal-trace-1 trace file in http://gaia.cs.umass.edu/wireshark-labs/wireshark-traces.zip. The first and second ARP packets in this trace correspond to an ARP request sent by the computer running Wireshark, and the ARP reply sent to the computer running Wireshark by the computer with the ARP-requested Ethernet address. But there is yet another computer on this network, as indicated by packet 6 – another ARP request. Why is there no ARP reply (sent in response to the ARP request in packet 6) in the packet trace?
虽然ARP是广播的,但是回复结果不是广播的,仅仅是正确寻找的IP地址才会返回应答,因此一台可以抓到ARP请求,答复将发送给直接发出请求的计算机